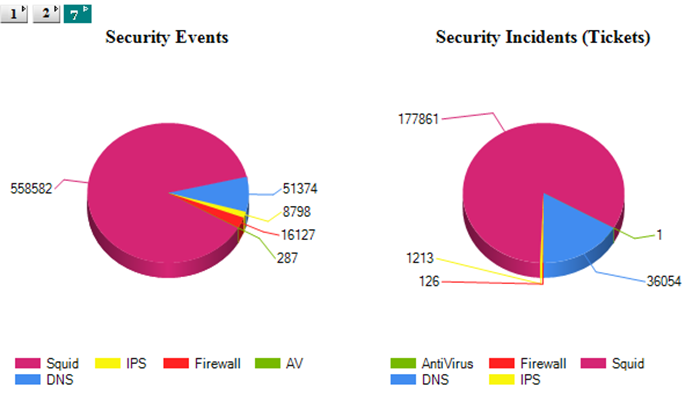
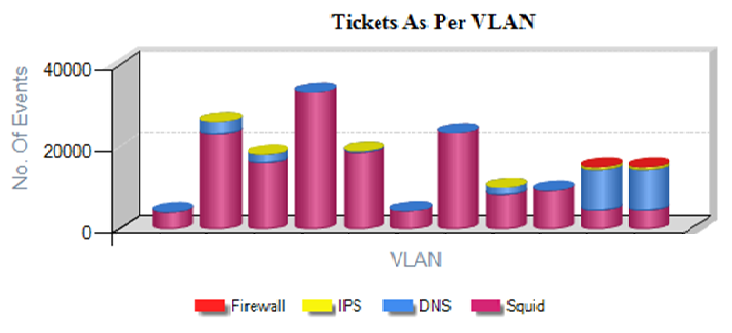
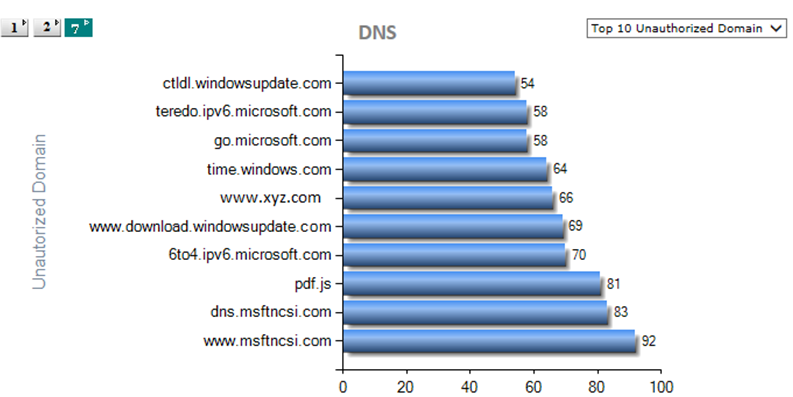
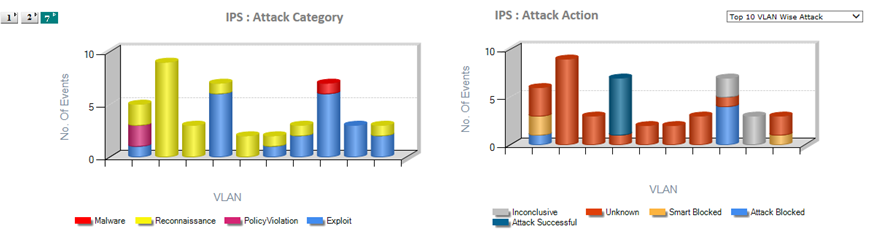
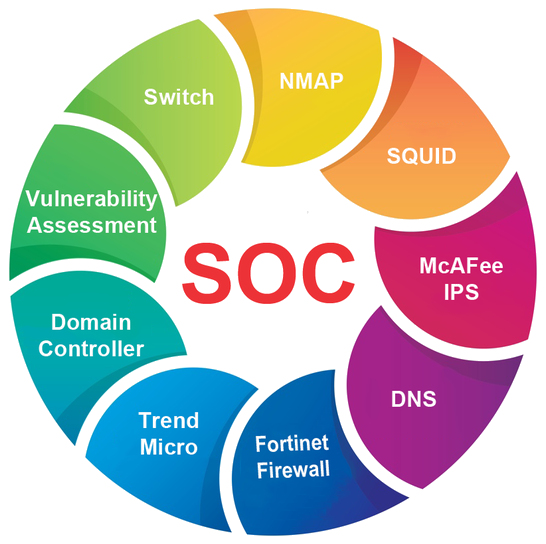
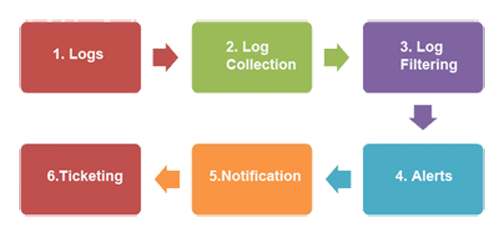
Centralized view of all IT assets that impact the IT Security. Consolidate alerts and alarms from multiple interrelated sources to create notification and alerts. Centralize remediation and response to Security Events across the IT Network. Wants to Build one large centralized SOC.
Challenges in Implementing SOC
- Single SOC is an ideal situation.
- But in diverse networks, implementing and operationalizing SOC is going to be huge challenge.
- Also in multi-tier networks, a platform that allows local admins to view the security event data and alerts is also required.
- Also implementing the solutions/modules that will provide inputs are generally not in place, resulting in SOCs to run deaf/blind.
- And, there is no structured plan to implement systems (IT, Human or Procedural) and modules to address outputs of the SOCs.
- Structured Roadmap to implement a Security Infrastructure will make SOC implementation easy and benefits tangible.
Network Aware Security Infrastructure
- Identifying incident remediation using:
- Network Traffic patterns/type and content
- Dynamically changing access control of network components to quarantine, island or shape network behavior.
- Dynamic NAC systems.
- Network recovery and remediation servers.
- Organization with diverse IT networks and assets and locations have found it easier to build Micro-SOCs(μSOC) at each geographical/IT network.
- The Security events/alerts/alarms from these μSOC can be consolidated in a global SOC.
- Implementing the μSOC is fast and less painful. And can be done independently from the implementation of the other μSOCs.
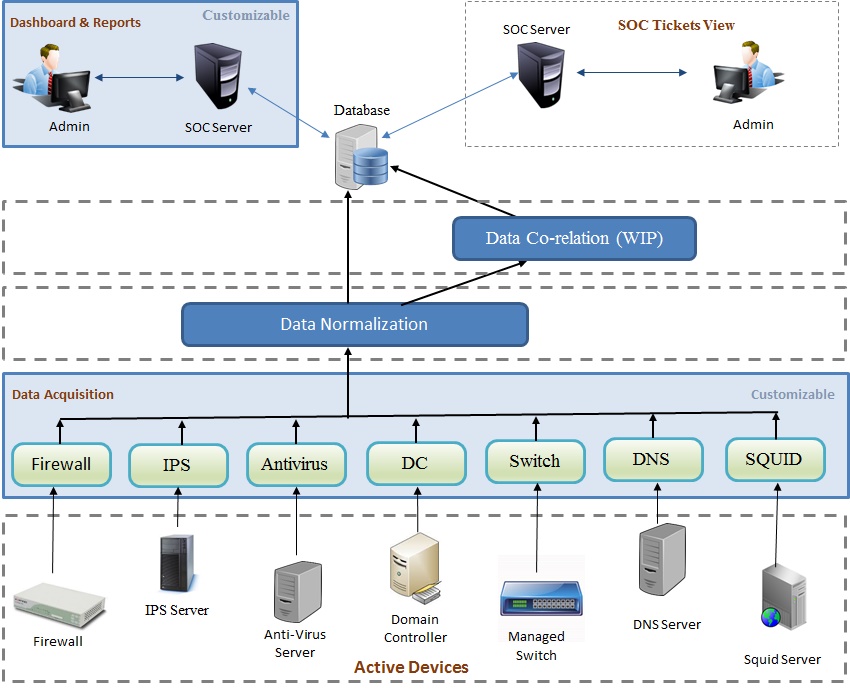
NMAP
- Get NMAP sacn logs, and collate this in a log table.
Alerts
- Raise alert when new IP/Device is seen.
- when there is a change in IP and MAC combination.
Squid Proxy Server
- Get SQUID logs, and parse and get information from the logs.
Alerts
- Access/Attempt after office hrs(Configurable by us).
- Download exceeding a value(Configurable).
- Access to sites other than main domain.
DNS
- Get DNS sacn logs, and parse and get information from the logs.
Alerts
- Try to attempt unauthorized Host/Domains.
- Which user has trying to access unauthorized Host/Domains.
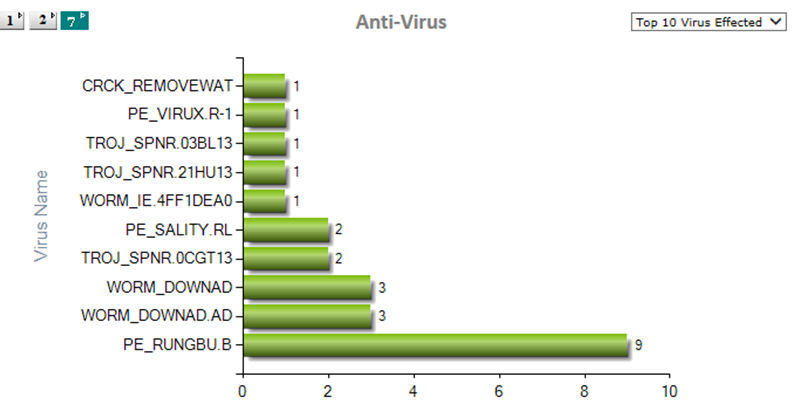
Trend Micro Anti-Virus
- Using SNAMP Traps.
Alerts
- When a AV/Malware is identified.
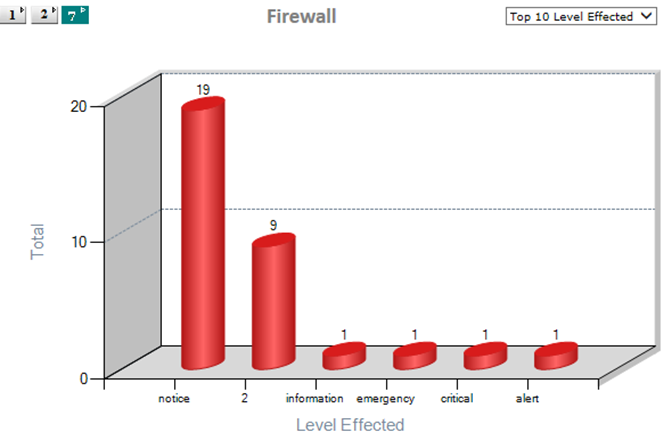
Fortinet Firewall
- Using SNMP Traps and SysLog Events.
Alerts
- Firewall events.
- Changes in firewall policies
SCCM
- SCCM APIs.
Alerts
- Patch missing information.
- Hardware change information.